
Protecting
Intellectual Property, Employee and Consumer
Data, and Peace of Mind
In
today's turbulent world, many U.S. authorities state
hacking of networks and intrusions to steal or change
data are a form of terrorism just as a serious threat
as ISIS. From our government agencies to hospitals,
retailers to banks, movie studios to utility companies,
unscrupulous individuals and governments are trying
to gain control of equipment running electrical
power plants and water dams, to stealing employee
data as social security numbers and medical records.
No
matter what the illegal intrusion is, it can cost
your organization more than the money it would take
to fix your IT department's security. Think as...
paying credit service companies as LifeLock to cover
1000's of employees against further losses due to
unauthorized purchases. And have you considered
the damage to your organization's reputation in
the marketplace? Employee morale? Consumers confidence
being shaken using their credit and debit cards
in the future on your brand?
The
cold hard truth for any Fortune 500 CEO or SMB business
owner, and of course CISO's and CTO's is that...
no company is safe from attempts of network
intrusions because criminals and foreign governments
have nothing to lose by trying!
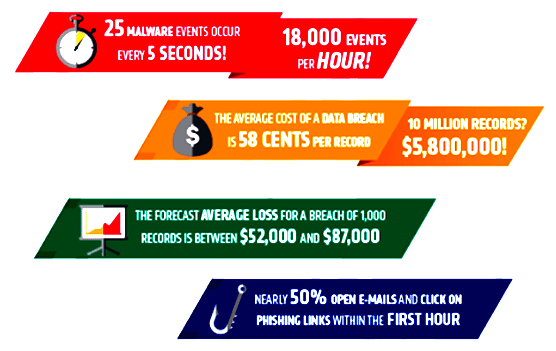
Just
a few 2015 cyber statistics at-a-glance:
-
Cyber
security incidents have surged 38%
since 2014.
-
Malicious
cyber attacks cost US $300B to $1
Trillion a year!
-
Data
breaches average $154 per record,
while the average cost per data
breach has reached $3.79M.
-
Attackers
often have more than 200 days before
being discovered.
-
Privilege
misuse is #3 out of nine attack
patterns found in 96% of all breaches,
according to the 2015 Verizon
Data
Breach Investigations
Report
-
While
deal makers are generally
aware of the effect
that cyber security
risks can have on
a pending M&A
deal, 78 percent “believe
cyber security is
not analyzed in great
depth or specifically
quantified as part
of the M&A due
diligence process.”
-
Asked
which stage of an
attack is the most
difficult to mitigate:
61 percent of IT security
executives cited privileged
account takeover;
versus 44 percent
in 2014
What
is your organization's cyber security
disconnect?
-
80
percent of board members say that
cyber security is discussed at most
or all board meetings, yet, two-thirds
of CIOs and CISOs say senior leaders
in their organization don’t
view cyber security as a strategic
priority.
-
Despite
almost daily reports revealing
the contrary, 44% of organizations
still believe they can keep attackers
off their network entirely.
-
28%
of organizations claim to have a
“problematic” shortage
of cyber security skills on-staff
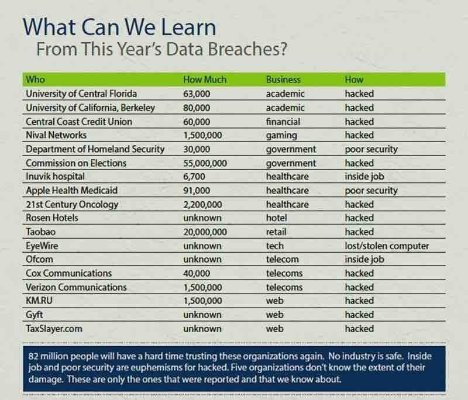
Which
Industry are you in? How lucky do you
feel?
UBB's
cyber security division, CyberSecurityLock, provides
services that address 8 domains organizations must
look at in their IT department:
- Security
and Risk Management (PCI Data Security
Standards, Federal Information Security Management
Act (FISMA) compliance, HIPAA, Sarbanes-Oxley, and
Gramm-Leach-Bliley Act (GLBA), and other Laws, Regulations,
Business Continuity Plans)
• Confidentiality, integrity, and availability
concepts
• Security governance principles
• Compliance
• Legal and regulatory issues
• Professional ethic
• Security policies, standards, procedures
and guidelines
- Asset
Security (Protecting Security of Assets)
• Information and asset classification
• Ownership (e.g. data owners, system owners)
• Protect privacy
• Appropriate retention
• Data security controls
• Handling requirements (e.g. markings, labels,
storage)
- Security
Engineering (Engineering and Management
of Security)
• Engineering processes using secure design
principles
• Security models fundamental concepts
• Security evaluation models
• Security capabilities of information systems
• Security architectures, designs, and solution
elements vulnerabilities
• Web-based systems vulnerabilities
• Mobile systems vulnerabilities
• Embedded devices and cyber-physical systems
vulnerabilities
• Cryptography
• Site and facility design secure principles
• Physical security
- Communication
and Network Security (Designing
and Protecting Network Security)
• Secure network architecture design (e.g.
IP & non-IP protocols, segmentation)
• Secure network components
• Secure communication channels
• Network attacks
- Identity
and Access Management (Controlling Access
and Managing Identity)
• Physical and logical assets control
• Identification and authentication of people
and devices
• Identity as a service (e.g. cloud identity)
• Third-party identity services (e.g. on-premise)
• Access control attacks
• Identity and access provisioning lifecycle
(e.g. provisioning review)
- Security
Assessment and Testing (Designing, Performing,
and Analyzing Security Testing)
• Assessment and test strategies
• Security process data (e.g. management and
operational controls)
• Security control testing
• Test outputs (e.g. automated, manual)
• Security architectures vulnerabilities
- Security
Operations (Foundational Concepts, Investigations,
Incident Management, and Disaster Recovery)
• Investigations support and requirements
• Logging and monitoring activities
• Provisioning of resources
• Foundational security operations concepts
• Resource protection techniques
• Incident management
• Preventative measures
• Patch and vulnerability management
• Change management processes
• Recovery strategies
• Disaster recovery processes and plans
• Business continuity planning and exercises
• Physical security
• Personnel safety concerns
- Software
Development Security (Understanding, Applying,
and Enforcing Software Security)
• Security in the software development lifecycle
• Development environment security controls
• Software security effectiveness
• Acquired software security impac
|
Subscribe
to
Our
Newsletter
ULTIMATE
Policy
~We
believe in speaking plainly and not using sales hyperbole
as so many do. Thus, one goal drives us, a 100% honest discussion
with our clients. You are the SME (Subject Matter Expert)
on why you are in business and how you conduct it.
After
a candid conversation about this, only at this time will we
make recommendations, if needed, Then we will explain
WHY we recommend the course of actions and WHY it will have
a positive impact on your bottom line.
Fair
enough?
Contact
Info

220
Newport Center Dr.Suite
11Newport
Beach, CA 92660
- Corp:
949-689-2240Fax:
949.644.4329 sales@UBB.com





Business
Opportunities
_____
Your
Advertisement Here
Business
Services
Your
Advertisement Here
|









